Can an E-Signature Be Forged? What Actually Happens in Disputes
An e-signature can be forged, but modern e-signature software and secure e-signature systems are designed to generate audit evidence that makes forgery detectable and legally provable.
Electronic signatures now sit at the center of how contracts are executed across finance, real estate, healthcare, HR, and SaaS. As adoption has accelerated, so has scrutiny. The real question courts ask today is no longer whether a document was signed electronically, but whether the signing process reliably proves who signed, how they signed, and whether the document was altered afterward.
Unlike wet-ink signatures, which rely heavily on visual comparison and subjective analysis, e-signatures generate objective, timestamped, system-level evidence. That difference fundamentally changes how disputes are evaluated and resolved.
Key Takeaways
E-signatures can be forged, but secure platforms leave traceable forensic evidence.
Most disputes hinge on audit trails, authentication, and document integrity.
Courts prioritize intent and identity over visual signature appearance.
Proven forgery typically voids the agreement and triggers fraud liability.
E-signatures often provide stronger evidence than wet-ink signatures.
What Does Forging an E-Signature Actually Mean?
Forging an e-signature means executing a signing action without the signer’s authorization, not merely copying how their signature looks.
This distinction is critical. Many people assume forgery is about handwriting similarity. Legally, it is about authority and intent. If someone signs a document using your identity, credentials, or access without permission, the signature is forged even if it visually matches nothing at all.
Courts do not evaluate whether a signature looks authentic. They evaluate whether the signing event can be reliably attributed to the correct person acting intentionally.
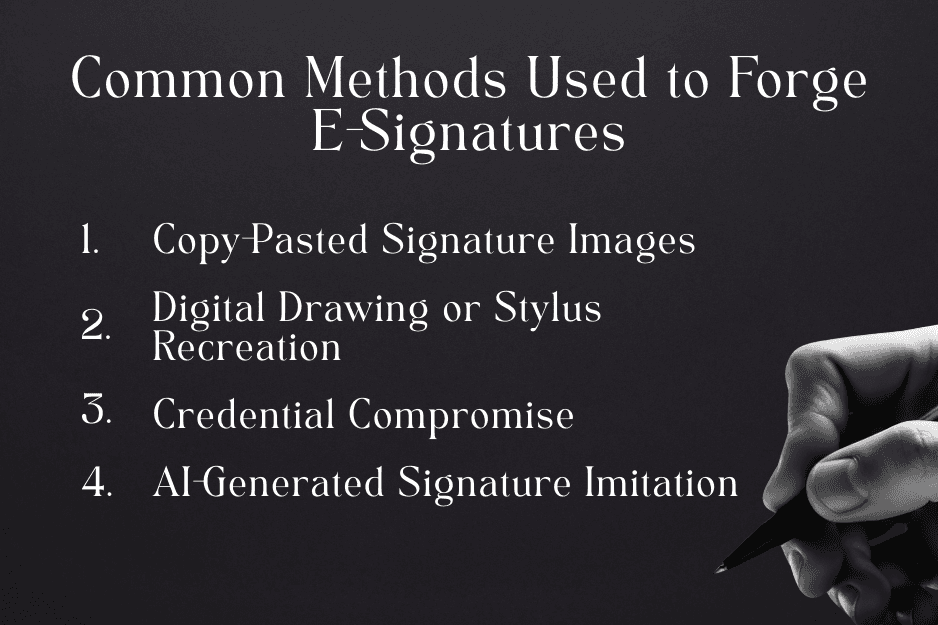
Common Ways E-Signatures Are Forged in Practice
Most e-signature forgery attempts rely on unauthorized access or reused signature images rather than sophisticated technical attacks. These methods exploit weak identity verification and user behavior, not failures in cryptographic systems. As a result, disputes usually center on access control rather than signature appearance.
Copy-Pasted Signature Images
Image-only signatures are the weakest form of electronic signing. A scanned or pasted image can be reused endlessly and carries no intrinsic identity proof. Because the image is detached from any authentication event, it provides no evidence of who applied it or under what circumstances. Courts generally view image-based signatures as decorative rather than evidentiary unless supported by strong surrounding documentation.
Digital Drawing or Stylus Recreation
Hand-drawn signatures on touchscreens can be imitated. Similarity alone does not establish authenticity or intent. Even highly accurate recreations fail to prove that the signer personally executed the action at a specific time and place. Without supporting audit data, stylus-drawn signatures are treated similarly to wet-ink signatures in disputes.
Credential Compromise
The most common real-world risk is account takeover. If someone gains access to a signer’s email or signing credentials, they can execute signatures that appear valid unless additional verification is required. This risk increases when signing links are forwarded, shared, or accessed on unmanaged devices. In disputes, credential compromise shifts the focus to security practices rather than document content.
AI-Generated Signature Imitation
AI can replicate handwriting styles, but it cannot replicate cryptographic bindings, audit logs, or signing context. As a result, AI-generated signatures fail quickly under forensic review. These signatures lack verifiable timestamps, identity linkage, and system-level proof of intent. Courts evaluate them as visual imitations, not valid execution events.
Why Secure E-Signatures Are Hard to Forge Undetectably
Secure e-signature platforms bind identity, intent, and document integrity into a single evidentiary chain. Forgery attempts must defeat multiple independent controls rather than a single visual marker. This layered design makes undetected manipulation statistically unlikely.
Audit Trails as Legal Evidence
Audit trails record every step of the signing process, including timestamps, IP addresses, device types, and action sequences. These logs are routinely admitted as evidence. They allow courts to reconstruct the signing event with precision rather than inference. Inconsistent or missing audit data is often more damaging than a disputed signature image.
Cryptographic Hashing and Tamper Detection
Documents are hashed at the moment of signing. Any change after signing alters the hash, immediately revealing tampering. This mechanism protects not only the signature but the entire document body. Even minor edits invalidate the original cryptographic fingerprint.
Digital Certificates and Identity Binding
Digital certificates link a signature to a verified identity using cryptographic keys. If the certificate does not match the signer, the signature fails validation. Certificates also establish non-repudiation by tying the signing action to a unique private key. This makes later denial technically and legally difficult.
Authentication Layers
Multi-factor authentication, knowledge-based questions, and biometric checks significantly raise the burden for forgery attempts. Each additional layer reduces reliance on a single credential or access point. In disputes, strong authentication shifts the burden toward proving intentional misuse rather than accidental access.
What Actually Happens When an E-Signature Is Disputed
E-signature disputes are resolved through digital evidence analysis, not handwriting comparison. The focus shifts away from how a signature looks and toward how the signing event occurred. Courts evaluate whether the signing process reliably links the action to a specific person acting with intent.
First, legal teams collect the signed document, full audit logs, authentication records, and any identity verification data generated during the signing process. Digital forensics specialists then examine timestamps, IP address consistency, device identifiers, hash integrity, and the sequence of actions taken by the signer. Handwriting experts play a limited role, if any, because visual similarity carries little evidentiary weight without supporting technical proof.
Courts look for consistency across all available data points. Does the signing location align with the signer’s known geography? Does the device match prior usage patterns? Do timestamps align with business communications or transaction timelines? When these elements conflict, the likelihood of forgery increases substantially.
How Do You Prove That Your E-Signature Was Forged?
You prove e-signature forgery by demonstrating that the signing event does not match your identity, intent, or control. The goal is not to show that the signature looks unfamiliar, but that the execution context is inconsistent with your actions or authority.
This may include evidence that you never received the signing request, that the IP address or device used is unfamiliar, or that the signing event occurred while you lacked access to your account or email. Security incident records, password reset logs, and breach notifications can further support claims of credential compromise. Platform-generated audit trails often provide the strongest proof because they are system-created, time-stamped, and resistant to manipulation.
Disputes frequently arise in sales, healthcare, real estate, and university environments, where speed, volume, and delegated workflows increase risk. In sales contexts, forgery claims often involve contracts sent to the wrong contact, links forwarded internally without authorization, signatures executed after verbal pressure but without clear intent, or agreements signed during account transitions or staff turnover.
A common mistake across these industries is focusing on whether the signature “looks wrong” rather than examining how the deal was executed. In sales disputes especially, parties may argue misunderstanding or miscommunication, but courts focus on whether the signing process reliably proves intentional consent at the moment of execution.
In civil disputes, the standard is typically preponderance of evidence, meaning it must be more likely than not that the signature was unauthorized. In criminal cases involving fraud, prosecutors must meet the higher standard of proof beyond a reasonable doubt. In both scenarios, the strength and consistency of the digital evidence often determine how quickly a dispute is resolved.
Legal Standards Courts Use to Evaluate E-Signatures
Courts assess e-signatures based on reliability, intent, and statutory compliance. The central inquiry is whether the signing process produces trustworthy evidence that a specific person agreed to specific terms at a specific time.
In the United States, enforceability is governed by the ESIGN Act and the UETA, which require that electronic signatures be attributable to the signer and retained in a form capable of accurate reproduction. In the European Union, validity is assessed under eIDAS, which classifies signatures based on the strength of identity verification and technical safeguards. Higher assurance levels carry greater legal weight.
Across jurisdictions, the core question remains consistent. Does the system reliably prove who signed, how they were authenticated, and that the document remained unaltered after execution? Courts care far more about process integrity than signature format.
What Happens If an E-Signature Is Proven Forged?
A forged e-signature invalidates the agreement and may trigger civil or criminal liability. Once forgery is established, the contract is generally treated as void because valid consent was never given.
The victim may seek restitution, damages, or declaratory relief depending on the harm caused by the forged agreement. In commercial contexts, this can include recovery of funds, reversal of transactions, or termination of obligations. The individual responsible for the forgery may also face fraud charges, particularly if the act involved deception, financial gain, or identity misuse.
Courts may additionally examine whether weak security controls contributed to the forgery. In some cases, inadequate safeguards can expose organizations to secondary liability.
Why Signatures Still Matter If Forgery Is Possible
Signatures matter because they formalize intent and accountability, not because they are impossible to fake. A signature creates a clear legal moment where obligations attach and rights are exchanged.
By signing, a party affirms agreement to specific terms and accepts the consequences of that agreement. This allocation of responsibility is foundational to contract enforcement. Without a signature, disputes often devolve into arguments over implied consent, verbal promises, or incomplete negotiations.
The real value of a signature lies in the surrounding evidence trail. In electronic systems, that trail often provides stronger proof of intent than traditional ink ever could.
E-Signatures vs Wet Ink in Real Disputes
E-signatures usually outperform wet-ink signatures in disputes because they generate objective proof. Digital signing systems capture data that handwritten signatures cannot, including precise timestamps, access paths, and document integrity checks.
Wet-ink signatures rely heavily on subjective handwriting analysis, witness testimony, and memory. These methods are vulnerable to interpretation, degradation over time, and incomplete records. By contrast, e-signatures produce structured, repeatable evidence that can be independently verified.
As a result, courts increasingly view electronic signatures as more reliable when disputes arise, provided the underlying system uses appropriate security controls.
Best Practices to Prevent E-Signature Forgery
Forgery risk drops dramatically when identity verification and access controls are layered and enforced. Prevention focuses on reducing unauthorized access rather than perfecting signature appearance.
Organizations using modern e-signature software should implement the following safeguards:
Require multi-factor authentication (MFA) to ensure signing access cannot be granted through email compromise alone
Limit signing windows so links expire after a defined timeframe, reducing reuse or forwarding risk
Restrict link forwarding or require re-authentication if a signing link is accessed from a new device or location
Monitor unusual access patterns, including unfamiliar IP addresses, devices, or geographic locations
Log all signing actions with detailed audit trails to preserve forensic evidence if a dispute arises
Educate signers on credential security, including the risks of shared devices, saved passwords, and public networks
Strong prevention is procedural, not cosmetic. Effective forgery defense depends on disciplined execution of identity controls and access policies, not on how a signature looks on the page.
FAQs About E-Signature Forgery and Disputes
Can an e-signature be challenged years after a document is signed?
Yes. An e-signature can be challenged as long as the contract is still legally enforceable under applicable statutes of limitation. Audit trails and document retention practices become critical as time passes.
Who has the burden of proof in an e-signature forgery dispute?
The party alleging forgery typically bears the burden of proof. Once a reliable audit trail is presented, the burden may shift to showing unauthorized access or lack of intent.
Can an employer be held responsible for a forged employee e-signature?
Yes. Employers may face liability if inadequate access controls, shared credentials, or poor security practices enabled the forgery.
Are mobile-signed e-signatures treated differently in disputes?
No. Mobile e-signatures are evaluated using the same standards as desktop signatures, with device metadata often strengthening attribution rather than weakening it.
Does clicking “I agree” count as an e-signature in disputes?
Yes. Courts generally treat clickwrap and consent-based acknowledgments as valid e-signatures if intent, attribution, and record integrity are provable.
Can forwarding a signing link invalidate an e-signature?
Forwarding alone does not invalidate a signature, but it can weaken attribution if access controls and authentication are insufficient to identify the actual signer.
What role does email evidence play in e-signature disputes?
Email headers, delivery records, and access timestamps are often used to corroborate audit trails and establish whether the signer received and accessed the document.
Can an e-signature be partially valid if only one signature was forged?
In some cases, yes. Courts may enforce portions of an agreement if the forged signature is not material to the contract’s core obligations.
The Real Question Is Not Whether Forgery Is Possible, but Whether It Is Provable
E-signature forgery is not a theoretical risk, but it is rarely invisible. Modern electronic signing systems were designed with dispute resolution in mind, not just convenience. When identity verification, audit trails, and document integrity controls are properly implemented, the evidentiary record often tells a clearer story than handwritten ink ever could.
Courts do not expect perfection. They expect reliability. The deciding factor in most disputes is whether the signing process can credibly demonstrate who signed, how they were authenticated, and that the document remained unchanged after execution. When those elements align, allegations of forgery tend to collapse quickly. When they do not, even a visually familiar signature can fail.
For individuals and organizations alike, the takeaway is practical rather than abstract. The strength of an e-signature is not defined by how it looks, but by the quality of the evidence behind it. In disputes, that evidence determines enforceability, liability, and outcomes long after the document is signed.
At ROGER, we approach e-signatures as legal records, not just transaction tools. Our signing workflows are designed to generate defensible audit evidence that holds up in disputes, compliance reviews, and real-world enforcement scenarios. Book a call to ensure your agreements stand up under real legal scrutiny.